Hot Topics
Ongoing Cyberattack Targets Exposed Selenium Grid Services for Crypto Mining
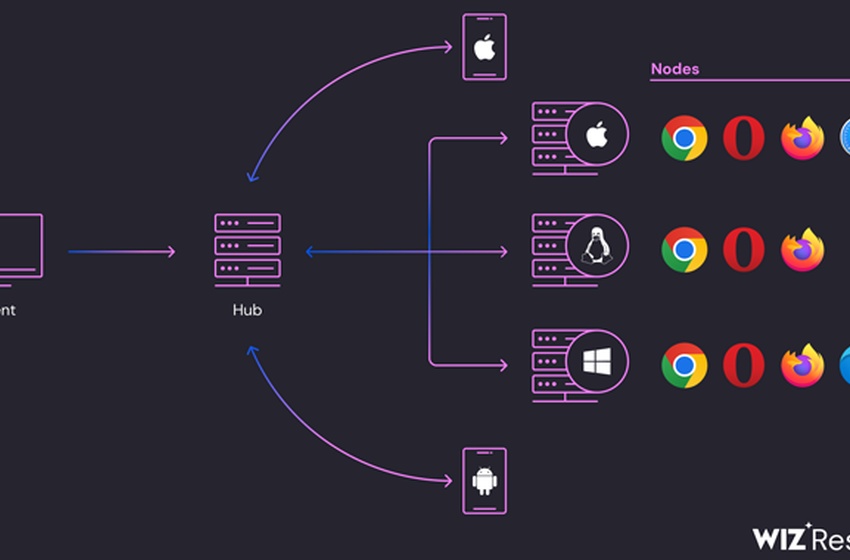
Cybersecurity researchers are sounding the alarm over an ongoing campaign that's leveraging internet-exposed Selenium Grid services for illicit cryptocurrency mining.
Bitcoin Magazine CEO Plans $15M Fundraiser for Trump in Nashville: Washington Post
Bitcoin Magazine CEO David Bailey is reportedly organizing a fundraiser for former President Donald Trump’s reelection campaign, with a target of $15 million.
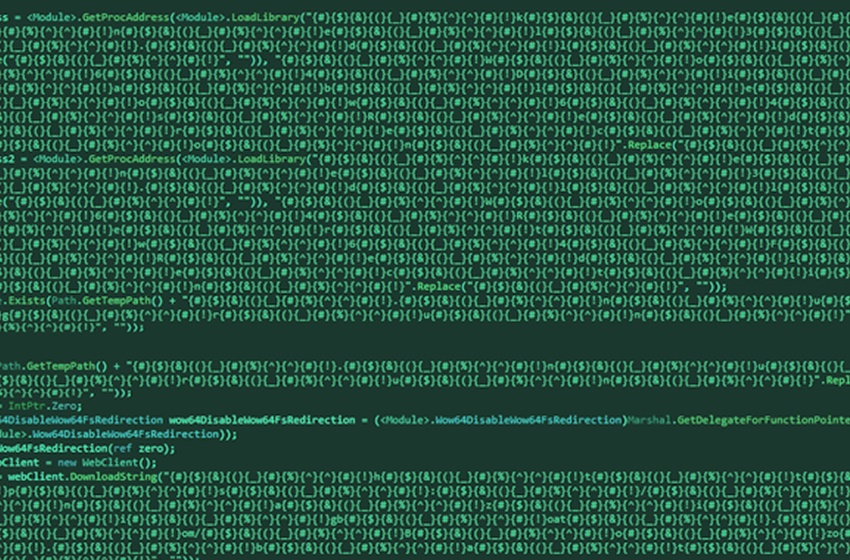
60 New Malicious Packages Uncovered in NuGet Supply Chain Attack
Threat actors have been observed publishing a new wave of malicious packages to the NuGet package manager as part of an ongoing campaign that began in August 2023, while also adding a new layer of stealth to evade detection.
Bitcoin Sinks Under $61K as One Trader Sticks to $150K Prediction This Year
U.S.-listed ETFs ended a five-day inflow streak with $13 million in net outflows on Tuesday, while concerns of the Mt. Gox distribution may have contributed to a sell-off.
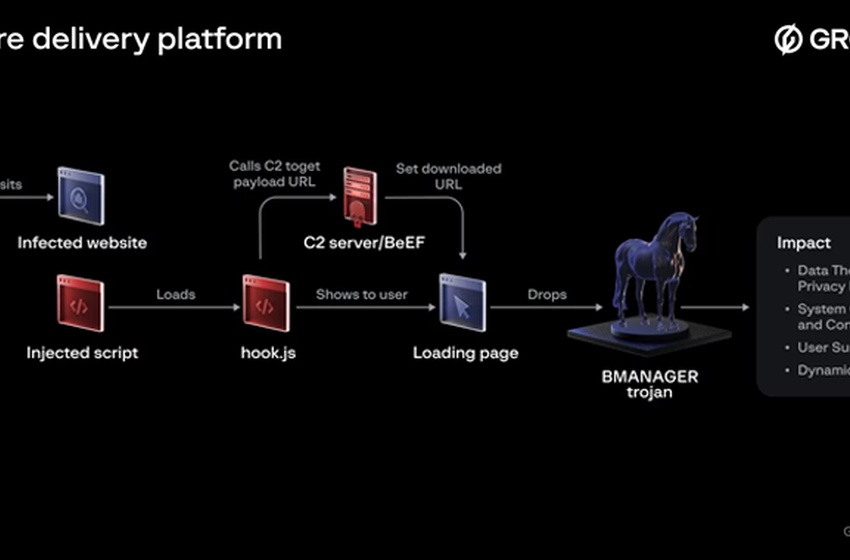
New Cyberthreat 'Boolka' Deploying BMANAGER Trojan via SQLi Attacks
A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER.
Arid Viper Launches Mobile Espionage Campaign with AridSpy Malware
The threat actor known as Arid Viper has been attributed to a mobile espionage campaign that leverages trojanized Android apps to deliver a spyware strain dubbed AridSpy.
© 2020, Gnuhost. All rights reserved